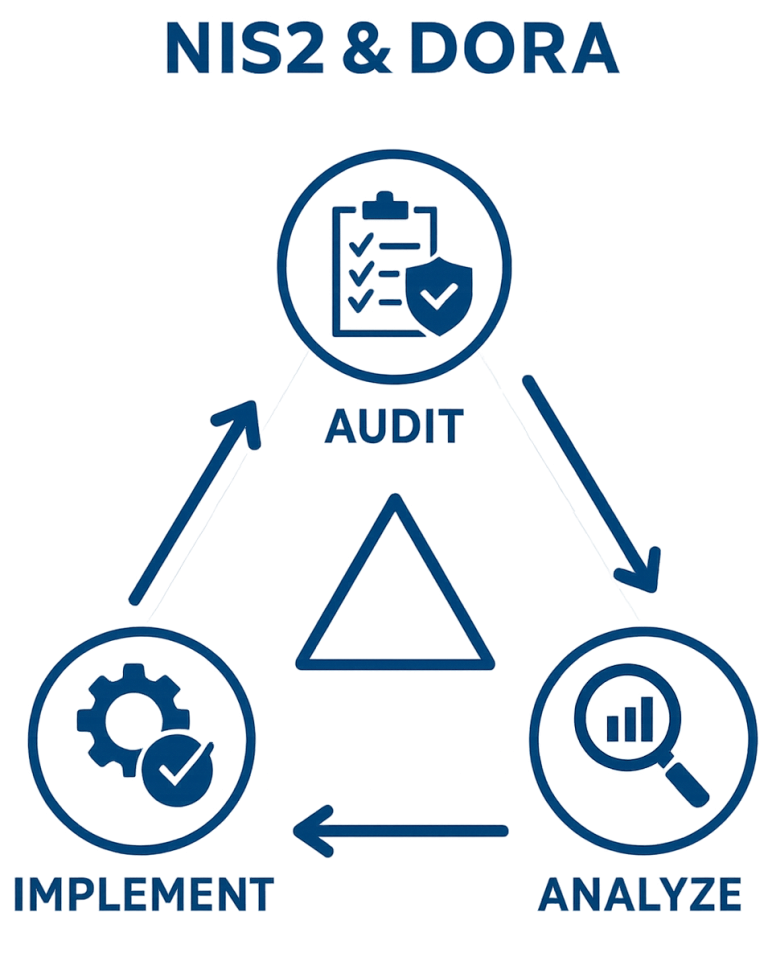
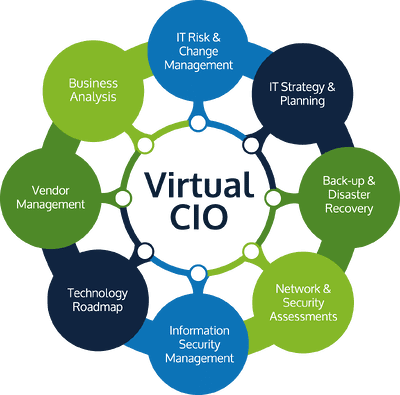
AI in 2025 MSP vCIO Strategy – Strategic Insights for Clients
In this blog, I explore how AI in 2025 MSP vCIO strategy is evolving from hype to real business value. Artificial Intelligence (AI) is no longer just a buzzword—it has become a strategic priority for organizations worldwide. As a vCIO working within a Managed Service Provider (MSP), one of the most valuable conversations you can…